Research on Low Duty Cycle MAC Protocol in Wireless Sensor Networks Because of its huge application prospect, wireless sensor network has become an active research branch in the field of computer and communication. Proper communication protocol is of great significance to reduce wireless communication energy consumption and prolong network life. The low duty cycle MAC (Media Access Control) protocol greatly reduces the idle monitoring energy consumption of the communication module through the node's sleep mechanism. This paper analyzes and compares the typical protocols, and gives further research directions. Keywords wireless sensor network, media access control, low duty cycle introduction The wireless sensor network is composed of many small sensor nodes through wireless multi-hop self-organization, a multi-disciplinary and highly cutting-edge research field. With the miniaturization of sensor nodes, the energy of most nodes in the design is limited, and the wireless sensor network is centerless, self-organizing, multi-hop, etc., which makes the design of the MAC protocol facing huge challenges. The main function of the media access control (MAC) protocol is to control the access and occupation of wireless media by the sensor node's message transmission, ensuring the overall performance of the network. Through the analysis of the existing system, it can be seen that the radio frequency module of the communication part of the wireless sensor network node is the largest energy-consuming component in the node, and is the main goal of optimization. The MAC protocol directly controls the radio frequency module, which has an important influence on the power consumption of the node, and is the key to ensuring the efficient communication of the wireless sensor network. This article mainly discusses the basic problems of MAC protocol in wireless sensor networks. 1 MAC address In wireless sensor networks, if the MAC protocol is to avoid listening and stay in sleep for as much time as possible, then the MAC address is very important. The MAC address is used to identify the next-hop sensor node during data forwarding. The MAC address is included in the unicast MAC packet. After receiving the packet, the node checks the routing table of the node to determine the MAC address of the next hop. This process continues until the data packet reaches the destination node. At the same time, the node determines which data packets have not arrived, and the nodes that have not reached the data can enter the sleep mode. Wireless sensor networks generally use wireless multi-hop communication, and the MAC address has spatial multiplexing characteristics: as long as the node MAC address is guaranteed to be unique among the transmission neighbor nodes, the neighbor node identification function that does not affect the MAC address is reused outside the transmission neighbor node. In the MAC layer, this way of overhearing avoidance is a very important method of saving energy consumption. The MAC address allocation protocol can be divided into two types of distributed allocation: network uniqueness and local uniqueness. The address allocation protocol must consider the asymmetry of the network link. As shown in Figure 1, asymmetry means that node A can hear node B, but conversely, node B cannot hear node A. Assuming that all nodes only communicate with two-way neighboring nodes, any two-way node of node A must have completely different addresses. Moreover, the address of any unidirectional input node must be different from the address of all bidirectional nodes. The node's link relationship is divided into two-way link, one-way input and one-way output. In order to cope with the time-varying and random factors of wireless links, this neighboring node protocol should be run repeatedly, in order to update and confirm the link relationship between neighboring nodes in real time. When node A completes the analysis of the status of neighboring nodes, it starts broadcasting messages, and A's bidirectional link node and unidirectional output node send back INFO messages as a response. In a similar way, node A knows the identity of each neighboring node. After the node A passes the threshold period, it knows the situation of the single-hop node and the two-hop neighboring nodes around it. If there is an address conflict in the single-hop node of node A, it sends a CONFLICT message. After receiving the message, the conflicting node starts a new round of address selection. After node A successfully executes the address allocation algorithm, it has its own address. This address allocation algorithm has the lowest probability of collision. In the content-based MAC protocol, the MAC address is an indispensable energy-saving measure, which can avoid interception of surrounding neighboring nodes. 2 Low duty cycle protocol and wake-up problem The ideal state of a node should be that when a packet is transmitted to this node, the node is always in the receiving state. When the node itself wants to send a packet, the node is always in the sending state. At other times, this node is always dormant. The low duty cycle (low duty cycle) protocol keeps nodes in as many sleep states as possible to minimize the communication activity of sensor nodes. To implement this mechanism, periodic wakeup methods have been introduced in several MAC protocols. As shown in FIG. 2, the node is dormant most of the time, and is periodically woken up to receive data from other nodes. A complete wake-up cycle includes sleep period and monitoring period. The ratio of the length of the listening period to the wake-up period is the duty cycle. The sparse topology and energy management (STEM) protocol provides a solution to the idle monitoring problem. Two different channels, namely the wake-up channel and the data channel, are shown in Figure 3. The data channel is generally in sleep mode unless data is sent or received. In the data transmission state, the data channel only implements the MAC protocol. In the wake-up channel, time is divided into several wake-up periods of fixed length T. A wake-up period is further divided into a listening period with a length of TRX≤T and a sleep period, which represents the period during which the transceiver of the wake-up channel enters the sleep mode. If a node enters the monitoring period, the receiver of its wake-up channel should be turned on and wait for the received signal. If no information is received within TRX time, it will switch to sleep mode again. Otherwise, the data channel transceiver will initiate a packet transmission. The SMAC protocol provides mechanisms to reduce idle monitoring, collision collisions and crosstalk. Contrary to STEM, SMAC does not require two different channels. It uses a periodic wake-up scheme, that is, each node alternately changes a fixed-length listening period and a fixed-length wake-up period according to a predetermined schedule. Unlike STEM, SMAC's listening period can be used to receive and send packets. As shown in Figure 4, the monitoring cycle of node x is further divided into three stages: SYNCH, RTS, and CTS. The SYNCH phase is the synchronization phase. Node x receives SYNCH packets from its neighbors. The group contains the schedules of neighboring nodes. Node x stores these schedules in the Schedule table. The SYNCH stage is further divided into time slots. The neighboring nodes of x use CSMA to compete for the channel, and there is a corresponding back-off. If no data is received in any of the previous time slots, each neighbor node y wishing to send a SYNCH packet can randomly pick up a time slot and start transmission. In other cases, node y will return to sleep mode and wait for node x to be woken up next time. Node x does not need to broadcast in every wake-up period of node y. In the RTS phase, which is the request sending phase, node x listens to RTS packets from neighboring nodes. In SMAC, the RTS / CTS handshake method is used to reduce the impact of data packet collisions and hidden terminal problems, and adjacent nodes in this stage may compete. The CTS phase is the clearing phase. If node x receives an RTS packet in the previous stage, node x sends a CTS packet and then exchanges data. Node x listens periodically throughout the synchronization period to understand the status of its neighbors. Nodes at border locations must adhere to two or more different schedules to broadcast their SYNCH packets and send data. Therefore, these nodes will consume more energy than nodes whose neighbors all use the same schedule. SMAC uses a periodic wake-up method, allowing most of the node's data to stay in sleep mode, but it also brings a certain communication delay. In addition, it will occupy a lot of storage space to cache data, which is particularly prominent in wireless sensor networks with limited resources. The MD (MediaTIon Device) protocol is compatible with the peer-to-peer communication method specified in the IEEE 802.15.4 standard. The protocol provides reliable communication that does not require high-precision clock synchronization between large-scale, low-duty-running nodes. The MD protocol allows nodes in a wireless sensor network to periodically enter a sleep state and stay in awake mode only for a short time to receive packet data from neighboring nodes. The protocol introduces the concept of dynamic synchronization (dynamic synchronizaTIon), which means that synchronization can be achieved without the sending node having to wait for the receiving node's inquiry beacon. As shown in Figure 5, the node is dormant most of the time and sends out an inquiry beacon when it wakes up. As a non-stop arbiter, the MD node coordinates the temporary synchronization of the two nodes to transmit data by receiving the RTS (request to send) sent by the information transmission node and the query beacon of the target node. The way to set up special MD nodes is called "fixed MD". Since the MD nodes are constantly in the receiving state and do not meet the low energy consumption requirements of the network, a distributed MD protocol is proposed, that is, the nodes become MDs randomly. In this way, the average duty cycle of each node can still be very low, and the entire network maintains an asynchronous network with low power consumption and low cost. Compare the above several protocols in the following aspects, as listed in Table 1. Table 1 Comparison of various protocol features 3 MAC protocol analysis and outlook This paper introduces a related technology of MAC protocol. Through analysis of several MAC protocols, it can be seen that the energy efficiency problem is a basic problem of the MAC protocol of wireless sensor networks. Therefore, we pay special attention to methods that can significantly reduce the overall energy consumption of the system. The method that can bring the node into the dormant state whenever needed is an effective way to save energy. To meet this requirement, this design uses low duty cycle or wake-up technology. The sleep mechanism reduces energy consumption but increases latency, and there are contradictions among multiple performance indicators. Further research is needed to find out how to balance each optimization index according to application requirements. Existing MAC protocol research rarely pays attention to the specific application of the network, and some specific applications require the MAC protocol to be specifically optimized for certain indicators or certain indicators. Therefore, the MAC protocol needs to provide a flexible mechanism to adapt to a variety of different application networks. Jilin Province Wanhe light Co.,Ltd , https://www.wanhelight.com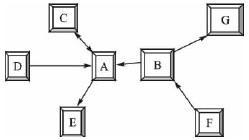
Figure 1 Bidirectional link node, unidirectional input node, unidirectional output node 
Figure 2 Periodic wake-up method 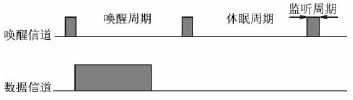
Figure 3 STEM duty cycle of a single node 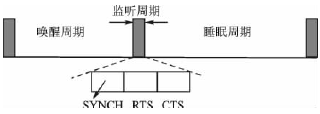
Figure 4 SMAC schematic 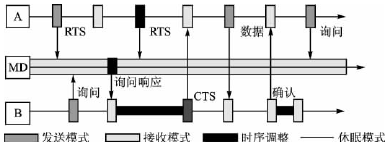
Figure 5 MD protocol 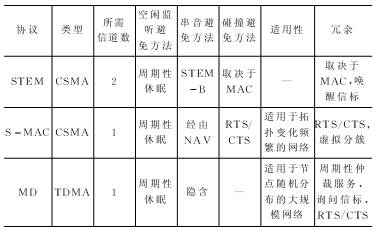
May 11, 2020