Introduction to the basic tasks and requirements of key management
**Introduction to Key Management**
A key, in the context of encryption, refers to a set of cryptographic techniques used in both personal and enterprise environments. These keys are essential for securing sensitive data, protecting user privacy, and maintaining the confidentiality of business information. Key management involves the entire lifecycle of keys, including their generation, distribution, storage, use, replacement, and destruction.
Key management systems are crucial, especially in military or high-security computer networks, where users may be mobile, have complex affiliations, and require coordinated operations. This complexity demands a robust and secure approach to managing keys to ensure that only authorized parties can access protected information.
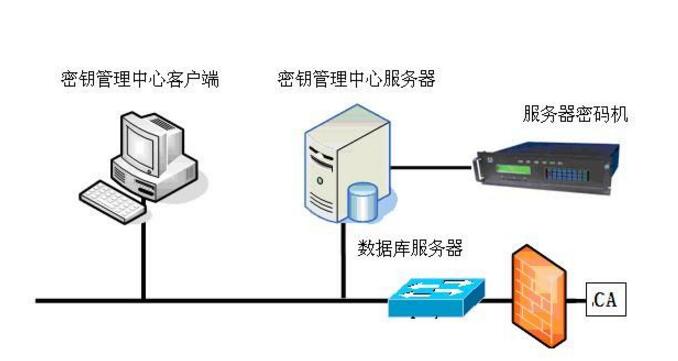
**Types of Keys**
a) **Basic Key or Initial Key**: This is a key assigned by the system to a user and may remain with them for an extended period. It is also known as a user key. Together with a session key, it initiates and controls a key generator that produces a key stream for data encryption.
b) **Session Key**: A session key is used between two communicating parties during a single session. It can act as a data encryption key when protecting transmitted data or as a file key when securing stored files. Session keys can be agreed upon by the communicating parties or dynamically issued by the system, making them also known as private keys.
c) **Key Encryption Key (KEK)**: This key is used to encrypt session or file keys during communication. Each node in a network typically has its own KEK.
d) **Host Master Key**: The host master key is used to encrypt the key encryption key and is stored securely within the host processor.
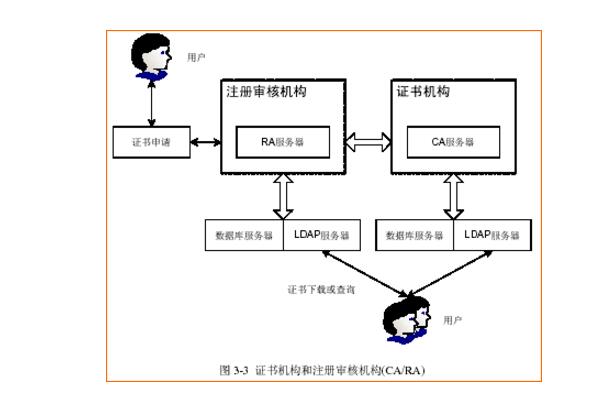
**Purpose and Scope of Key Management**
The purpose of key management is to standardize how keys are used in product development and production processes to prevent unauthorized access or data breaches due to improper handling.
**Scope of Application:**
This policy applies to the management of key usage in all stages of product design, development, and manufacturing within the company.
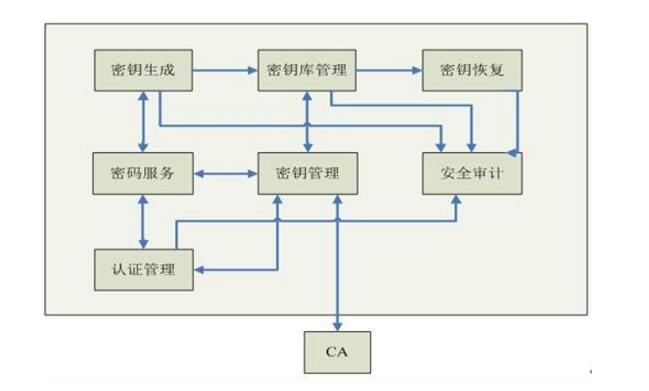
**Basic Tasks and Requirements of Key Management**
**1. Generation of Security Data**
Before personalization begins, the appropriate encryption keys must be generated according to the defined procedures. At a minimum, the following keys should be created:
- **Issuer Master Key (KMC):** Used to derive KMAC, KENC, and KDEK.
- **KMAC:** Used to lock the application area of a financial IC card and verify data integrity.
- **KENC:** Used to generate encrypted data for the card and verify host-side encryption.
- **KDEK:** Used to encrypt confidential data written to the card during personalization.
- **Master Key (MDK):** Used to export UDK for online card authentication and issuer authentication.
- **Issuer's Public-Private Key Pair:** Generated by the issuing bank and used to create public key certificates.
- **Key Exchange Key (KEK):** Used to encrypt confidential data in the personalization input file.
- **Transport Key (TK):** Used to encrypt confidential data during transmission from the data preparation system to the personalization system.
- **ICC Public-Private Key Pair:** Used for DDA and CDA/AC algorithms. The public key must be signed by the issuing bank’s private key.
- **MDKENC and MDKMAC:** Used for encrypting and verifying bank script data.
**2. Formation and Distribution of Keys**
The security of asymmetric keys (like SM2/RSA) depends on the protection of the private key. Risks include solving the ECDLP problem, decomposing the RSA modulus, or private key leakage. To mitigate these risks, key lengths, key quality, and physical protection methods must be strictly controlled.
Keys should be generated using secure devices with random number generators and tamper-resistant mechanisms. Private keys must never be generated on untrusted devices like PCs. Public keys should be transmitted via secure channels such as certificates or MACs, while private keys must be encrypted and transported securely.
For symmetric keys, the generation process must be conducted in a physically secure environment. Dual control and secure storage practices are essential to prevent key exposure.
**3. Preservation of Root Key Plaintext Data**
Once key data is received, the responsible manager must verify its integrity. Any uncertainty about the data’s authenticity requires immediate notification to the sender. Hard copies of key data must be stored in secure envelopes, and all access must be logged and auditable.
**4. Storage of Other Key Data**
Asymmetric and symmetric keys should be stored in secure environments. PC boards providing encryption services can function similarly to HSMs, but they must be protected against attacks. All keys outside of the card or HSM must be under dual control. HSMs should clear memory when threats are detected and be housed in secure locations.
**5. Personnel Management**
Key managers must be appointed by the technical vice president and undergo strict confidentiality checks. They must be permanent employees, not temporary staff or consultants. Backup personnel should be selected using the same rigorous criteria as primary managers. Key responsibilities include secure storage, verification, and logging of key usage. They must also oversee the secure destruction of expired keys and ensure proper key injection into secure modules.

Since its establishment in 2016, Jiangsu Yunbo Intelligent Technology Co., Ltd. has continuously explored and developed unmanned aerial vehicles with various functions. Currently, we have independently developed and produced agricultural unmanned aerial vehicles, transport carrying unmanned aerial vehicles, and racing time crossing aircraft. We hope to explore and promote the contribution of unmanned aerial vehicles to humanity in a broader field with peace loving friends around the world.
Flight controller: F3/F4/F7/RF/Kiss.
Engines: 2305/2306/2407/2408/2507/2807/2810/2812.
ESC: 30A-70A.
Battery: 4S-6S.
Propellers: 7 inches.
Max Load: 3 Kg
Application: 7-inch FPV Drone

3K Carbon Fiber drone Frame,Quadcopter Freestyle RC FPV Drone Frame,FPV Drone Frame 7inch
Jiangsu Yunbo Intelligent Technology Co., Ltd , https://www.fmodel-ai.com